i can't detect my laptop on the work network
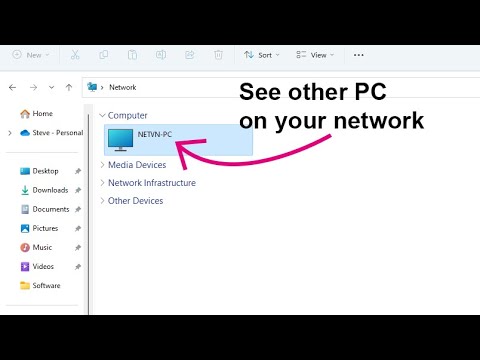
Title: Fix Cant See Other Computers on Network Windows 1011
Channel: NETVN82
Fix Cant See Other Computers on Network Windows 1011 by NETVN82
Laptop Vanished From Work Network? This Trick Will SHOCK You!
Gone in 60 Seconds (…or Less!): Recovering Your Missing Work Laptop
Have you ever experienced that heart-stopping moment? The one where you realize your work laptop has seemingly vanished into thin air? The panic sets in. You start to retrace your steps. Where did you last have it? Was it at the office? The coffee shop? The train? Breathe. Before you completely lose it, let’s explore how to reclaim that missing tech treasure.
The Phantom Laptop Phenomenon: A Modern Mystery
Losing a laptop is more than just misplacing a gadget. It’s a potential data breach. It’s lost productivity. It’s a major headache. The modern workplace relies heavily on these portable powerhouses. So, when one goes missing, it isn't just inconvenient; it can be downright scary. Frequently, the actual disappearance is caused by a simple mistake. Perhaps you left it in a taxi, or maybe you just forgot it at a meeting. But occasionally, more sinister forces could be at play. Thus, we need to be prepared.
Early Detection is Key: Your Digital Detective's Checklist
The sooner you act, the better your chances of recovery. First, stop. Take a deep breath. Now, think. When did you last see your laptop? Where were you? Try to build a mental timeline. Consider every little detail. This will help to narrow down your search area.
- Notify IT Immediately: This is the most crucial step. Your IT department can remotely lock or wipe the laptop. They can also often track its location. Do this without delay.
- Check Cloud Backups: Did you back up your important files? Hopefully, you did! Cloud services automatically save your work. This can save you hours of potential heartbreak.
- Review Recent Activity: Check your email, calendar, and other online accounts. These can provide clues about where the laptop might have been.
Embrace the Power of Tracking: Unleash Your Inner Sherlock
Several software programs offer laptop tracking capabilities. They employ GPS, Wi-Fi triangulation, and other methods. So, if you’ve enabled these features, your chances of finding your device improve drastically. Now, we get into the cool part.
- Built-in Features: Many laptops come with built-in tracking. Check your device’s settings. Look for names like “Find My Device” or “Laptop Tracker.”
- Third-Party Software: Consider installing tracking software. Services like Prey or LoJack provide excellent tracking and security features. These tools are worth the investment.
- Report it Stolen: If you have reason to believe your laptop was stolen, you should report it to the police. Provide them with the laptop's serial number and any other relevant details.
The “Shocking” Trick: Securing Your Data (Even If the Laptop’s Gone)
Even if you can’t recover the laptop immediately, there are steps you can take. These steps that will protect your sensitive information. Think of it as damage control, but for your data. Importantly, this is where that "shocking" value comes in.
- Remote Wiping: Your IT department can also remotely wipe the laptop. This deletes all the data. It’s a drastic measure, but it’s a vital one to prevent a data breach. This action protects your company and your personal information.
- Password Protection and Encryption: Always use strong passwords. They are your first line of defense. Encrypt your hard drive. This makes your data unreadable to unauthorized users.
- Change Your Passwords: Immediately change the passwords for all your accounts. This includes work email, social media, and any other accounts you access on your laptop.
Beyond the Laptop: Preventing Future Disappearances
Losing a laptop once is enough. Prevention is key to avoiding a repeat performance. Therefore, you need to make some changes to ensure future security and minimize chances of loss.
- Develop a Routine: Always pack your laptop in a designated bag. Make it a habit. This reduces the chances of leaving it behind.
- Secure Your Laptop: Never leave your laptop unattended in public. Use a privacy screen to protect your screen's information. Consider a security lock for added protection.
- Educate Employees: Provide training to your employees. This will address data security awareness. This also makes sure everyone is aware of the proper protocols. Thus, everyone is on the same page.
Wrapping Up: Stay Calm and Carry On
Losing a work laptop is stressful, there is no doubt about it. However, it doesn't have to be a disaster. By acting quickly and following these steps, you can increase your chances of recovery. Even if the laptop doesn't resurface, you can still protect your data. Remember to stay calm and take decisive action. The situation is rarely, if ever, as bad as it seems initially. Therefore, follow the tips above. Your peace of mind – and your data – will thank you. The end result? Less shock, and hopefully, a reunited laptop.
Laptop Work Hacks: Boost Productivity & Conquer Your To-Do List!Laptop Vanished From Work Network? This Trick Will SHOCK You!
We've all been there, haven't we? That sinking feeling in your gut as you realize your laptop, the lifeline to your work, your projects, maybe even your entire career, has vanished. One minute it's there, humming away, a beacon of productivity; the next? Poof! Gone. Vanished into the digital ether, leaving you staring at your desk, equal parts bewildered and panicked. Trust me, the first time my laptop disappeared from my work network, I nearly had a heart attack. I started imagining it: stolen, lost in the abyss, maybe even undergoing some elaborate government conspiracy. Okay, maybe the government conspiracy was a bit much, but the point is, the initial reaction is always fear.
1. The Dreaded Disappearance: Your Laptop's Houdini Act
The immediate reaction is panic. You frantically check under the desk, behind the monitor, anywhere and everywhere a laptop could conceivably hide. But it's not there. Then, the realization hits: it’s not just missing from your immediate physical space. It’s gone from the network. It's not showing up when you ping it; the shared drives are empty. It’s like your digital companion, the one you relied on daily, just… evaporated. This is where the real investigation begins.
2. Before You Freak: Breathe and Take Stock
Before you start picturing your digital life being auctioned off on the dark web (again, maybe a bit dramatic, but the feeling is real!), take a deep breath. Panic rarely helps. We need to think clearly. Let's assess the situation logically. Did you move it? Did someone else? Is it a simple network glitch? Ask yourself these questions first.
3. Network Detective 101: Simple Checks Before the Panic Sets In
Okay, so deep breaths taken. Let's troubleshoot. Think of yourself as a digital detective, armed with simple tools.
- Check the Obvious: Is the power cord plugged in? Is the laptop actually on? I know it sounds silly, but you’d be surprised how often this is the problem. (Guilty as charged, on multiple occasions).
- Network Connectivity: Can you access the internet? Can you connect to other devices on the network? This helps determine if the problem is isolated to your laptop or a wider network issue.
- Recent Changes: Did you update any software? Install any new programs? Sometimes, a faulty update can cause connectivity issues.
- Ping Test: Open Command Prompt (Windows) or Terminal (Mac) and try to "ping" your laptop's IP address. This is a simple test to see if the network can "see" the device. If it's unreachable, there's a problem.
4. The Usual Suspects: Common Culprits in Laptop Disappearances
Sometimes, the solution is straightforward. Let's look at some of the most common culprits:
- Accidental Disconnection: Maybe the Ethernet cable got unplugged. Maybe the Wi-Fi simply dropped the connection.
- Power Outage/Battery Drain: Did the power go out? Did the battery die? Simple, but easily overlooked.
- Network Issues: Sometimes, the network itself is the problem –router glitches, server downtime, etc.
- Temporary Software Glitches: A software conflict or minor update can temporarily disconnect your device.
- User Error: (Let's be honest, it happens to the best of us!) Did you accidentally shut it down and forget?
5. The SHOCKING Trick: Unveiling the Hidden Network Sniffer
Now, for the trick that might just blow your mind. (And hopefully get your laptop back). This isn't about magic; it's about smart digital sleuthing. We’re not talking about hacking or illegal activity, but using network tools legally and responsibly to track down your missing laptop. The key here is a network sniffer.
What is a network sniffer? Think of it as a specialized listening device for your network. It captures and analyzes network traffic, allowing you to see what devices are communicating and what they're saying. Crucially, it can often reveal the IP address of a device even if it's being sneaky and trying to hide. This is where things get interesting.
6. Choosing Your Weapon: Selecting the Right Network Sniffer
There are several network sniffers available, some free, some paid, each with its strengths. For our purposes, we need something relatively easy to use, especially if you're not a networking guru.
- Wireshark: This is the gold standard, a powerful and versatile tool. It can be a bit overwhelming for beginners, but the potential is tremendous.
- Tcpdump: A command-line tool that's included in many Unix-like operating systems. It's less user-friendly than Wireshark but very powerful.
- Network Monitor: A more user-friendly interface, great for beginners to inspect network traffic within a simplified view
7. Setting Up Your Digital Hunting Ground: Installing and Configuring the Sniffer
This will depend on the tool you chose, but the general process is similar.
- Download and Install: Follow the installation instructions for your chosen sniffer.
- Select Your Network Interface: Choose the network adapter that connects your computer to the network (e.g., Ethernet, Wi-Fi).
- Start Capturing Traffic: Launch the sniffer and start capturing network traffic. Be patient; it may take a while to collect sufficient data.
8. Deciphering the Digital Whispers: Analyzing Network Traffic
This part can feel like learning a new language, but don't worry, we'll break it down. Your sniffer will display a stream of data packets. You're looking for any traffic related to your missing laptop.
- Look for Suspicious Activity: Are there any unexpected devices communicating with your network? Any traffic that looks unusual?
- Filter by MAC Address: If you know your laptop's MAC address (a unique identifier), you can filter the results to show only traffic from that device. (If you don't know it, you may be out of luck. But, it's still worth trying.)
- Look for IP Addresses: Even if the laptop is trying to hide, its IP address might still be visible sometimes.
- Look for Port Numbers: Determine which ports your laptop is utilizing, to find it on your network.
9. The Moment of Truth: Finding Your Laptop's Digital Footprint
This is where the "shock" comes in. If you're lucky, your network sniffer will reveal your laptop's IP address, even if it's trying to be stealthy. You may find it connected to a different place. This knowledge is power.
10. From IP Address to Location: The Next Steps
Finding the IP address is just the first step. You won't instantly know the full location of the device, but you'll be able to narrow it down.
- Check DHCP Server: Your network's DHCP server (often your router) logs IP address assignments. This log might reveal when and where your laptop was last active.
- Contact IT Support: If you are using a work laptop, inform your IT department immediately. They have tools and access beyond what you have. They can help.
- Report to Authorities: Depending on the situation and the information you gather, you may need to involve the police.
11. Password Protection: Securing Your Digital Fortress
While the network sniffer can help you find it, it's important to consider the security of your data. If the laptop is in the wrong hands, you need to protect your information.
- Change Passwords: Immediately change all passwords on your accounts, especially those related to your work.
- Enable Remote Wipe: If your laptop has remote wipe capabilities (like on many corporate devices), use it to erase all data.
- Report The Theft: Report the theft to the proper authorities.
12. Preventing Future Disappearances: Proactive Measures
Once you get your laptop back (or even if you don’t), it's time to harden your defenses. Here's how to prevent a recurrence.
- Enable Full Disk Encryption: This is essential. It encrypts all your data, rendering it useless to anyone who doesn't have the password.
- Use Strong Passwords: And update them regularly.
- Install Antitheft Software: These programs can track your laptop's location, even if it's offline, and help you recover it.
- Back Up Your Data Regularly: This is the most critical step. If the worst happens, you won't lose everything.
- Use A VPN: A VPN encrypts data sent over the network, which prevents potential hackers from intercepting valuable information.
13. Practical Tips and Tricks
Let’s keep it practical.
- Keep meticulous records: Note the IP address, MAC address, and other details.
- Train employees: Educate your team on cybersecurity
- Be aware of your surroundings: Don’t leave your laptop unattended.
14. The Human Factor: Beyond the Tech
Technology is essential, but don't forget the human element. Cybersecurity is
Laptop Screen SHOCKER: How This Tiny Miracle Works!7 Ways to Fix a Computer That Can't Find or Connect to Wifi Windows 10 Laptops & Desktops

By Ask A Computer Geek 7 Ways to Fix a Computer That Can't Find or Connect to Wifi Windows 10 Laptops & Desktops by Ask A Computer Geek
Fix WiFi Not Showing in Settings On Windows 10 Fix Missing WiFi 2025
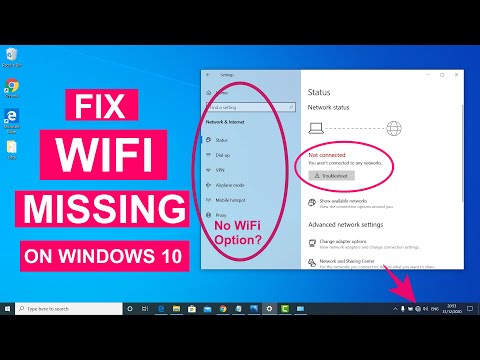
By Sandeep Singh Fix WiFi Not Showing in Settings On Windows 10 Fix Missing WiFi 2025 by Sandeep Singh
How to Fix WiFi Not Showing Up on Windows 10 - Howtosolveit

By Howtosolveit How to Fix WiFi Not Showing Up on Windows 10 - Howtosolveit by Howtosolveit

Title: Not connected no connections are available windows 7 laptop
Channel: IT Magics
Not connected no connections are available windows 7 laptop by IT Magics
Laptop Volume Buttons DEAD? FIX THIS NOW!
Laptop Vanished From Work Network? This Trick Will Shock You!
A chill runs down your spine. The familiar weight of your company laptop, usually nestled in its usual spot, is gone. Vanished. Poof. Whether you're working remotely, at the office, or somewhere in between, the disappearance of your work laptop is a situation fraught with anxiety. Beyond the immediate panic, there's the potential for data breaches, the disruption to your workflow, and the fear of explaining the situation to IT and your superiors. But before you succumb to despair, breathe. We're here to guide you through a methodical process, offering a practical strategy to understand and, potentially, recover your missing device.
Initial Assessment: Taking Stock and Staying Calm
The first few moments after realizing your laptop is missing are crucial. Resist the urge to react impulsively. Instead, take a deep breath and perform a thorough assessment of the situation. This initial appraisal will inform your subsequent actions, potentially saving you valuable time and minimizing unnecessary distress.
Consider this: Where was the laptop last confirmed to be? When did you last use it, and where? Did you travel recently? Has anyone else had access to your work area or your belongings? Document the exact time you last saw the laptop and the circumstances surrounding its use. This information is vital for later investigations, both with IT and, if needed, with law enforcement.
Next, contemplate potential explanations. Is there a chance you simply misplaced it? Did you move it within your home or workspace, and it’s now in an unexpected location? Check all the usual places: under furniture, in bags, inside briefcases, in other rooms, and even in the car. Often, the solution is simpler than we initially assume.
Finally, and perhaps most importantly, remain calm. Panic clouding judgment will not help. Instead, maintain a clear head. This will allow you to systematically approach the problem and increase your chances of resolving it successfully. A methodical approach, beginning with a comprehensive understanding of the situation, is the cornerstone of effective recovery.
Essential Steps: Contacting IT and Security Protocols
Once you've conducted your initial assessment, the next crucial step is to contact your IT department immediately. Delaying this communication is detrimental; swift action is often the key. IT professionals are your primary resource in this situation. They possess the technical expertise and the access required to initiate a full investigation.
When contacting IT, provide them with all relevant details gathered during your initial assessment. Include specifics about the laptop’s make and model, its serial number (if you have it readily available), and its operating system. Also immediately report any sensitive data stored on the device, such as client information, financial records, or proprietary company data. This helps them prioritize their response and implement security measures.
Simultaneously, IT will likely activate several security protocols. These may include:
- Remote Wipe: If your company has implemented remote wipe capabilities, IT will attempt to erase all data from the laptop remotely. This is a critical step to prevent data breaches. This is often the first and most important action to be taken if data security is paramount.
- Account Lockout: IT will probably lock your user account to prevent unauthorized access to company resources via other devices. This helps to secure company data and prevent the compromise of your other devices.
- Location Tracking: Modern laptops often have tracking capabilities. IT will leverage these features if they're enabled. This allows them to pinpoint the laptop’s last known location, or to attempt to track its movement.
- Password Reset: Your passwords for company-related accounts might be immediately reset. This is standard practice to obstruct unauthorized access to your accounts.
Cooperate fully with the IT team. Answer all their questions accurately and thoroughly. Provide any additional information they request. The more information you give during this investigation, the higher the chances of locating your device.
Tracing the Digital Footprints: Utilizing Log Files and Activity Monitoring
Once IT has been apprised of the situation and security protocols have been initiated, the technical investigation begins. One of the most valuable tools in this phase is the analysis of system log files and activity monitoring.
Log files are created by your operating system and various applications. They capture a chronological record of actions performed on the computer, including login attempts, file access, software installations, and system events. IT professionals can leverage these logs to reconstruct the laptop’s activity before its disappearance.
IT can search for suspicious login attempts. Were there unauthorized logins attempted? Were there changes to user accounts or permissions? Were any files accessed or modified around the time the laptop went missing? These log entries are very important.
Further, activity monitoring tools provide IT with real-time insights into the laptop's usage patterns. These tools may track browsing history, application usage, and file transfers. This information can reveal crucial clues about the laptop's whereabouts and the actions of the person who may have gained unauthorized access to it.
By carefully scrutinizing log files and activity monitoring data, IT can often paint a detailed picture of the laptop's last known activities. This data helps determine if the device was stolen or misplaced. It can also provide evidence for law enforcement, should that become necessary.
The Power of Software: Utilizing Find My Device (and Similar Tools)
Many modern laptops come equipped with pre-installed or easily installable location-tracking software. This is particularly the case with Windows devices (Find My Device) and Macintosh computers (Find My Mac). These tools are indispensable in laptop recovery efforts.
If your laptop is linked to a Microsoft account, you can use the Find My Device feature to locate it, lock it, and even display a custom message on the lock screen. This feature utilizes the laptop’s built-in GPS, Wi-Fi, or cellular connectivity to determine its current location. The accuracy of the location is dependent on available network connectivity and whether location services are enabled on the device.
For Apple laptops, the Find My Mac feature offers similar functionalities. You can view the laptop's location on a map, play a sound to help locate it if it's nearby, lock the device, or remotely erase its data.
To utilize these tools effectively, ensure that location services are enabled on your laptop, and that your account is linked to it. Also, regularly check the status of the device in the Find My Device or Find My Mac app on other devices or through your account's online dashboard.
While these tools are not foolproof (they rely on the laptop being powered on and connected to the internet), they significantly increase your chances of recovery if the device has been stolen or misplaced. The more quickly you can activate these tools, the better your chances of success.
Reporting the Theft: Law Enforcement and Insurance Considerations
If, after exhausting all other avenues, the laptop remains missing, it is important to report the theft to law enforcement. Providing them with the details you gathered in the previous steps is important and useful.
When contacting the police, be prepared to provide as much information as possible. Include the laptop's make, model, serial number, and any unique identifying features. Provide the date and time the device went missing, the last known location, and a description of the circumstances surrounding the disappearance. IT may also provide information about the laptop's last known location and activity, which can be very helpful to the police.
Law enforcement will then initiate their investigation, which may involve contacting local pawnshops, reviewing surveillance footage, and conducting interviews. They may also be able to recover any data left on the laptop.
Besides law enforcement, notify your company's insurance provider. Many business insurance policies cover the loss or theft of company property, including laptops. To file a claim, you will need to provide documentation, such as a police report and a detailed description of the stolen device.
The insurance company will then assess your claim and determine the amount of coverage to which you are entitled. This can help offset the financial impact of the laptop's loss and potentially replace the missing device.
Data Security Mitigation: Preserving Sensitive Information
The loss of a laptop is not just about the physical device, but also about the data it contains. Protecting that data is essential to mitigating the potential damage caused by a data breach.
As mentioned earlier, the first step is remote wiping the device. In this case, the goal is to erase all data from the laptop remotely, making it inaccessible to anyone who finds or steals the device.
Beyond wiping, consider the types of data that were stored on the laptop. If it contained sensitive information, such as customer data or financial records, consider the steps needed to contain the data and comply with regulatory requirements. Assess the possible need to notify customers, clients, or affected parties, if their data was stored on the laptop. Your company will likely have detailed plans in place to deal with this.
If there are passwords, change them immediately. This protects your accounts from unauthorized access. Consider employing a password manager and using multi-factor authentication. These security enhancements can provide additional layers of protection for your account.
If the laptop contained confidential company data, review and update any non-disclosure agreements that may be in place. This helps protect the company's intellectual property. Moreover, review the scope of possible legal and regulatory requirements that apply to the handling of company data.
Preventative Measures: Future-Proofing Your Computer
While the recovery of a missing laptop is the immediate concern, the loss should also prompt a review of your data security practices. Implementing preventative measures can significantly reduce the risk of similar situations in the future.
One vital step is to enable encryption on your laptop. Encryption scrambles your data, making it unreadable to unauthorized users. In the event the laptop is lost or stolen, encryption can protect your sensitive business information.
Establish a strong password
