can your work laptop hear you

Title: Can Your Employer Listen to You Through Your Laptop Microphone - SecurityFirstCorp.com
Channel: SecurityFirstCorp
Can Your Employer Listen to You Through Your Laptop Microphone - SecurityFirstCorp.com by SecurityFirstCorp
can your work laptop hear you, does your work laptop listen to you, can your work computer hear you, can my work laptop listen to me, can employer listen through laptop, can my employer see what i do on my work laptop
Is Your Laptop Spying on You? The SHOCKING Truth!
Is Your Laptop Watching You? Unmasking the Digital Stalker
Believe it or not, your seemingly harmless laptop might be an uninvited observer. It's a chilling thought, isn't it? It’s easy to dismiss it as paranoia. However, the reality is considerably more complex. We dive deep into the digital labyrinth. This exploration aims to unveil uncomfortable truths. Let's unearth what lurks beneath the surface.
Hidden Cameras and Open Mics: Your Digital Fortress Breached?
Consider your webcam. It's a convenient tool for video calls. It also provides access for malicious actors. Moreover, they can potentially record everything around you. Think about the implications. You're potentially vulnerable. You might ask: What are the risks? The risks are multifaceted.
The microphone carries its own set of vulnerabilities. Imagine someone secretly recording your conversations. The potential is there, making privacy concerns very valid. After all, digital security is not just a technical issue. It's a matter of safeguarding your life. In the current age, this is more important than ever.
Software Spies: Malware and the Digital Footprint
Malware can infiltrate your system. Consequently, it can turn your laptop into a surveillance device. This software can be incredibly sophisticated. It can hide in plain sight. Also, it gathers data. This includes keystrokes, browsing history, and even screenshots. Therefore, it's sneaky and effective. It’s essential to stay informed.
Your digital footprint is constantly expanding. Every click, search, and purchase leaves a trail. Subsequently, this data can be exploited. Your personal information could be compromised. This also means the consequences are very significant. Therefore, online security is a priority. You must protect yourself.
Cybersecurity Best Practices: Fortifying Your Digital Life
Fortunately, you can fight back. There are steps you can take. They will strengthen your digital defenses. Therefore, you must proactively protect yourself. First, install and maintain robust antivirus software. Update your operating system and applications regularly. This will patch potential security vulnerabilities.
Also, be cautious when clicking links. Avoid suspicious websites and downloads. Never open email attachments from unknown senders. Consider using a virtual private network (VPN). In fact, it encrypts your internet traffic. This helps protect your data. It adds an extra layer of security. Besides, there are additional precautions you can take.
Webcam and Microphone Hygiene: Securing Your Privacy
Physical safeguards are important, too. Cover your webcam when not in use. A simple sticky note or a dedicated webcam cover works great. This prevents unauthorized access to your video feed. Regarding your microphone, be mindful of which applications have access. Review your privacy settings.
Regularly audit your device permissions. Disable the microphone for apps that don't need it. Stay vigilant about application permissions. Regularly review them to ensure they're appropriate. These simple actions offer substantial privacy protection. They also promote peace of mind.
Data Breaches and the Dark Web: The Aftermath of Exposure
Unfortunately, data breaches are frequent. Sensitive information is sometimes stolen and then offered on the dark web. Imagine your data becoming a commodity. It can be sold to the highest bidder. Often, the implications are far-reaching. Identity theft, financial fraud, and reputational damage are all possible.
Moreover, the dark web is a dangerous place. It's a hidden digital underworld. It’s where illicit activities thrive. Protecting your data is paramount. Vigilance, education, and proactive measures are key. So, take action to shield yourself.
Staying Informed: The Ongoing Battle for Digital Privacy
The digital landscape is ever-changing. New threats emerge constantly. Consequently, staying informed is crucial. Read cybersecurity news. Follow experts. Stay updated on the latest threats and trends. Knowledge is power.
Educate yourself regarding best practices. Learn how to navigate the digital world safely. Become your own digital security expert. Therefore, you can defend yourself against cyber threats. You'll be able to enjoy the benefits of technology. Do so without compromising your privacy. Finally, you are in control.
Asus Laptop Keyboard Disaster! (Some Keys Died!)Is Your Laptop Spying on You? The SHOCKING Truth!
Hey everyone! Let’s be real for a second. Your laptop. That sleek, portable window to the world. The one that streams your favorite shows, allows you to work from anywhere, and… well, could it be watching you? That’s the question that's been buzzing around the digital world, and honestly, it's a pretty unsettling one. This article isn’t about scaring you silly, but rather giving you the straight facts, cut through the noise. We're going to delve into the murky world of laptop surveillance, separating the sensational headlines from the genuine threats. Buckle up, because we’re about to uncover some shocking truths.
1. The Digital Peeping Tom: Why Should You Even Care?
Okay, so why should you even care if your laptop might be spying on you? Think about it this way: your laptop is a repository of your life. It holds your emails, your financial information, your browsing history, maybe even personal photos and videos. Imagine all that juicy intel falling into the wrong hands! It’s like having a digital diary that’s being read by someone you didn’t invite. Feeling a little creeped out? Good. That feeling is a healthy dose of digital vigilance. We need to be aware of the potential risks to protect ourselves. This isn't just about some shadowy figure peering into your webcam – it's about protecting your privacy, your identity, and your peace of mind.
2. The Webcam's Silent Stare: The Obvious Threat
Let's start with the most obvious culprit: the webcam. It's the tiny, unassuming lens perched above your screen. But what if that lens isn't just capturing your video calls? What if it’s recording you without your consent? It's a scary thought, and unfortunately, it's not just the plot of a bad horror movie. Hackers can gain remote access to your webcam, turning it into their personal surveillance device. They could be watching you in your living room, your bedroom, anywhere you use your laptop. It is like a silent intruder in your home, monitoring your every move. Not cool, right?
3. Microphone Mayhem: Listening In on Your Conversations
The microphone is another potential vulnerability. Think about it: if someone can access your webcam, they likely can access your microphone too. The potential implications are vast. They could be listening to your private conversations, gathering sensitive business information, or even recording your family's intimate moments. It’s like having a wiretap on your home. Imagine the conversations you’ve had – the secrets you've shared – being potentially exposed. Chilling, isn’t it?
4. Software Sleuths: How Malware Works
So, how exactly do these digital eavesdroppers penetrate your laptop's defenses? Usually, it starts with malware. Malware, short for malicious software, is designed to sneak onto your computer and wreak havoc. It can take many forms, from viruses to spyware. Sometimes, it piggybacks on seemingly harmless downloads, like free software or attachments in suspicious emails. Once installed, malware can exploit vulnerabilities in your operating system, giving hackers access to your webcam, microphone, and even all of your stored information. Think of it as a Trojan horse allowing unwanted guests into your digital castle.
5. Phishing: The Deceptive Invitation
Another common method is phishing. Think of it as a digital con. Phishing attacks involve tricking you into giving away your passwords, credit card details, or other sensitive information. The attacks often come disguised as legitimate emails or websites, designed to appear trustworthy. Clicking on a malicious link or entering your credentials on a fake site can give hackers the keys to your digital kingdom. It’s like trusting someone who is secretly a wolf in sheep's clothing.
6. Public Wi-Fi: A Cyber-Crouton
Public Wi-Fi networks, like those you find in coffee shops and airports, are notorious breeding grounds for cyberattacks. While convenient, these networks are often unencrypted, making your data vulnerable to interception. Anyone on the same network could potentially eavesdrop on your browsing activity, steal your login credentials, or even install malware on your laptop. Imagine your data being an open book for every eavesdropper on the public Wi-Fi network.
7. The Creepy Cookies: Tracking Your Every Click
Cookies are small text files websites place on your computer to track your browsing activity. They're often used to personalize your online experience, remembering your preferences and showing you relevant ads. However, cookies can also be used to track your browsing history across multiple websites, creating a detailed profile of your online behavior. It's like having a digital shadow that follows your every move.
8. Operating System Vulnerabilities: Weak Links
Every operating system (Windows, macOS, etc.) has vulnerabilities. These are weak spots in the software that hackers can exploit. Software developers release security updates to patch those holes, but if you don't update your operating system promptly, your laptop becomes more vulnerable. Think of it like leaving the doors of your house unlocked – a tempting invitation for potential intruders.
9. The Sneaky Spyware: Monitoring Your Every Move
Spyware is a type of malware specifically designed to monitor your online activity. It can record your keystrokes, capture screenshots, and even track your location. It’s like having a digital shadow that follows your every move. This information can then be used to steal your personal information and sell it to third parties.
10. The Shadowy Government: Surveillance Realities
Let's not forget the possibility of government surveillance. In some cases, governments may legally monitor your online activity, especially if you're suspected of criminal activity. This kind of surveillance often involves collecting data about your communications, your location, and your browsing history. It's a complex and often controversial topic, raising questions about privacy and freedom of speech.
11. Hardware Hacking: The Physical Threat
While less common, hardware hacking is a real possibility. A skilled hacker could potentially modify your laptop's hardware, such as the webcam or microphone, without you even knowing it. This type of attack is more difficult to pull off, but it's still a potential threat, especially for high-profile individuals. Think of it as digital sabotage, permanently embedded in your computer.
12. The "Deepfake" Deception: Beware Of Fabricated Evidence
"Deepfakes" are manipulated videos or audio recordings that appear to be genuine. With the rise of artificial intelligence, deepfakes are becoming increasingly sophisticated and realistic. Hackers could use deepfakes to impersonate you, spread misinformation, or damage your reputation. It's like a digital impersonation that can be used for malicious purposes.
13. Protecting Yourself: Simple Steps to Stay Safe
So, what can you do to protect yourself? The good news is, there are several simple, effective steps you can take:
- Keep Your Software Updated: Regularly update your operating system and all your applications. These updates often include crucial security patches that protect you from known vulnerabilities.
- Use Strong Passwords: Create strong, unique passwords for all your accounts, and use a password manager to store them securely.
- Install Antivirus Software: Invest in reputable antivirus software and keep it updated. This software will scan your computer for malware and can help prevent malicious programs from infecting your system.
- Be Careful What You Click: Don't click on suspicious links or open attachments from unknown senders. If something seems fishy, trust your gut.
- Enable Two-Factor Authentication: This adds an extra layer of security by requiring a second verification method, such as a code sent to your phone, when you log in to your accounts.
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic and hides your IP address, making it harder for hackers to track your online activity.
- Cover Your Webcam: When you're not using your webcam, cover it with a piece of tape or a dedicated webcam cover. It seems simple, but it is highly effective in preventing unwanted intrusions.
- Be Cautious on Public Wi-Fi: Avoid using public Wi-Fi networks for sensitive activities, such as online banking or accessing personal accounts.
14. The Power of Privacy: Taking Control
Protecting your privacy isn't just about avoiding cyberattacks; it's about taking control of your digital life. It means being mindful of the information you share online, being discerning about the websites you visit, and being proactive about protecting your data. It involves conscious choices and a commitment to digital safety.
15. The Future of Privacy: Constant Vigilance
The digital landscape is constantly evolving, with new threats emerging all the time. Staying informed about the latest cyber security risks is crucial. As technology advances, so will the techniques used by cybercriminals. Therefore, remaining vigilant and adapting your security measures will be essential in protecting your digital privacy.
Let's wrap this up!
So, the truth is, your laptop could be spying on you. It’s not a guarantee, and we don’t want to send you into a panic! The goal is to be aware of the risks, understand the methods, and take the necessary precautions. We hope this article has shed some light on the subject and equipped you with the knowledge to protect your digital life. Go forth and browse safely!
FAQs:
- How can I tell if my webcam has been hacked?
- Look for
Your company laptop may be spying on you

By KTLA 5 Your company laptop may be spying on you by KTLA 5
Fix Microphone Not Working on Windows 10
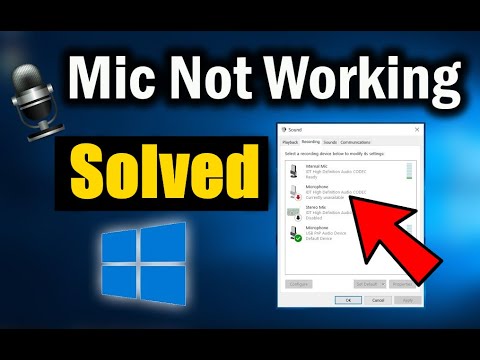
By The Geek Page Fix Microphone Not Working on Windows 10 by The Geek Page
Title: Shift Windows ctrl f5 shorts
Channel: jaywaddap
Shift Windows ctrl f5 shorts by jaywaddap
Laptop Working
Is Your Laptop Spying on You? The SHOCKING Truth!
The sleek, silent rectangle of your laptop. It’s a portal, a workhorse, a window to the world. But could it also be a two-way mirror, silently reflecting your life back to unseen watchers? The question isn't sensationalism; it’s a crucial examination of our digital reality. We delve into the potential surveillance capabilities embedded within your seemingly innocuous device, unearthing the unsettling truths about laptop security.
The Built-In Voyeurs: Understanding Your Laptop's Vulnerabilities
Your laptop, in its design, offers several points of access that, if exploited, can lead to comprehensive monitoring. Consider the following:
- The Webcam: The tiny lens perched above your screen is the most obvious, and often the most concerning, entry point. Modern webcams are capable of capturing high-definition video and audio, providing real-time insights into your surroundings and conversations. This access can be gained, often surreptitiously, through malicious software.
- The Microphone: Integrated microphones, similarly, can record every sound within their range. Conversations, private phone calls, ambient noise – all can be silently captured and transmitted. This capability poses a significant risk, especially in environments where sensitive information is discussed.
- Network Connectivity: Your laptop's connection to the internet is an open door. While it allows you to access the world, it also opens you up to potential intrusions. Hackers can exploit vulnerabilities in your operating system, web browser, or network configuration to gain access to your device and its data.
- Data Storage: Every file, document, image, and email stored on your hard drive or solid-state drive is a potential target. If compromised, your personal information, financial records, and confidential communications could be exposed.
- Location Services: Many laptops, particularly those with built-in GPS or Wi-Fi positioning capabilities, can track your physical location. This information can be valuable for targeted advertising or, in the wrong hands, for more sinister purposes.
Software Snoops: Malware, Spyware, and the Digital Threat
The threats aren't merely inherent in the hardware; they are amplified by malicious software. This software is designed to collect information about its victims.
- Malware: This broad category encompasses all types of malicious software, including viruses, worms, and Trojans. Malware can be designed to steal data, disable your computer, or provide remote access to your device.
- Spyware: As the name suggests, spyware is explicitly designed to spy on your online activities. It can track your browsing history, record your keystrokes, and capture screenshots.
- Keyloggers: These programs meticulously record every keystroke you make, including passwords, credit card numbers, and private messages.
- Remote Access Trojans (RATs): These sophisticated programs provide attackers with complete control over your computer, allowing them to access files, install software, and even control your webcam and microphone.
The Hidden Risks: Beyond the Obvious Threats
The threats extend beyond those that are easily recognized. Sophisticated methods bypass our awareness.
- Social Engineering: Hackers will sometimes use social engineering tactics to trick you into downloading malware or divulging sensitive information. This can involve phishing emails, deceptive websites, or impersonation.
- Supply Chain Attacks: These attacks target software updates or hardware components, injecting malware into the products you use every day. This means that even if you take precautions, you could still be vulnerable.
- Unsecured Wi-Fi: Connecting to public Wi-Fi networks without proper security measures can expose your laptop to eavesdropping and data theft. Attackers on the same network can intercept your internet traffic and steal your passwords and other confidential information.
- Data Breaches: Even if your laptop is secure, your data can still be compromised if the services you use are breached. Websites and online services are frequent targets of data breaches, and if your information is stored on their servers, you could be affected.
Taking Back Control: Safeguarding Your Privacy
Understanding the risks is the first step, but taking proactive measures is essential. The digital age demands vigilance.
- Webcam Security: Cover your webcam when it's not in use. This simple act is a highly effective safeguard against unauthorized access. Physical webcam covers, or even a piece of tape, can provide a visual deterrent and a physical block.
- Microphone Protection: Mute your microphone when you are not actively using it. This can be done through the operating system settings. Be mindful of background apps that could be using your microphone, such as voice assistants.
- Strong Passwords: Use strong, unique passwords for all your accounts. Avoid easily guessable passwords, such as birthdates or pet names. Use a password manager to generate and store complex passwords securely.
- Regular Updates: Keep your operating system, web browser, and all installed software up to date. Software updates often include security patches that address vulnerabilities.
- Antivirus and Anti-Malware: Install and maintain robust antivirus and anti-malware software. Run regular scans to detect and remove malicious software.
- Firewall: Enable your firewall to block unauthorized network access. A firewall acts as a barrier, protecting your computer from external threats.
- Secure Wi-Fi: Use secure Wi-Fi networks and avoid connecting to public Wi-Fi, or use a VPN (Virtual Private Network) when you do so to encrypt your internet traffic.
- Email Awareness: Be cautious about opening suspicious emails or clicking on links from unknown senders. Phishing attempts are common.
- Two-Factor Authentication (2FA): Enable 2FA wherever possible. This adds an extra layer of security by requiring a verification code, often sent to your phone, in addition to your password.
- Privacy-Focused Browsing: Use a privacy-focused web browser and configure your browser settings to block trackers and cookies.
The Silent Threat: Why You Need To Act Now
The digital landscape is constantly evolving. The threats to our privacy are more sophisticated, and the potential consequences are more severe. We must remain proactive in safeguarding our data.
- Identity Theft: Stolen personal information can be used to open fraudulent accounts, make unauthorized purchases, and damage your credit rating.
- Financial Loss: Hackers can steal your financial information and drain your bank accounts.
- Reputational Damage: Sensitive data, such as compromising photos or private messages, can be leaked online, causing reputational harm.
- Cyberstalking and Harassment: Stalkers can use your personal information and online activity to track and harass you.
- Corporate Espionage: Companies can become victims of industrial espionage, with confidential data stolen by competitors.
Conclusion: Your Digital Fortress
Your laptop is a powerful tool, but it's also a potential liability. By understanding the vulnerabilities, being aware of the threats, and taking proactive measures, you can transform your laptop into a secure digital fortress. The truth is not just shocking; it's a call to action. Protect your privacy, preserve your data, and stay safe in the digital world. The responsibility rests with you. Arm yourself with knowledge, practice vigilance, and take control of your digital destiny.

