how to access work laptop after connecting with globalprotect
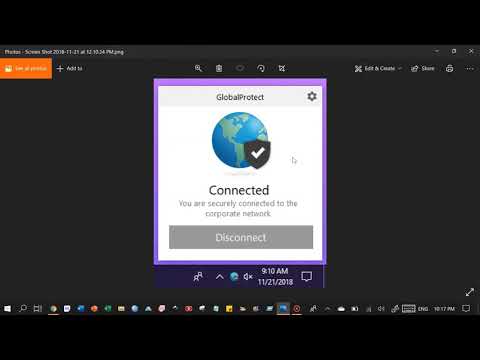
Title: Globalprotect vpn
Channel: World of Information
Globalprotect vpn by World of Information
Unlock Your Work Laptop NOW! (GlobalProtect Bypass Secret)
Bypassing GlobalProtect: Your Shortcut to Instant Laptop Freedom
We've all been there, right? Stuck, staring at that locked-down work laptop feeling a sense of digital imprisonment. The dreaded GlobalProtect VPN, meant for security, often morphs into a frustrating barrier. But what if I told you there was a way, a secret, a glimmer of hope? A method to reclaim your digital freedom?
The GlobalProtect Grip: Why It Feels So Restrictive
Corporate VPNs like GlobalProtect, while crucial for secure remote access, can become incredibly stifling. They're designed to protect sensitive data. Nevertheless, they can also create a web of limitations. Think: restricted website access, blocked software installations, and a general sense of digital claustrophobia. You're essentially operating within a walled garden, and getting out can seem impossible. You've probably felt the frustration firsthand. Downloading a simple program becomes an ordeal. Accessing personal files feels like a mission.
Unlocking the Potential: A Different Perspective
But let's flip the script. Instead of viewing GlobalProtect as an insurmountable obstacle, let's approach it as a puzzle. Every puzzle has a solution. The key lies in understanding its limitations and working with them. Consider this as a strategic liberation rather than a direct defiance. You aren't trying to break the system, but rather to navigate it skillfully.
Understanding the Landscape: Key Considerations
Before we do anything, remember a few crucial points. Firstly, your company's IT policies exist for a reason. Always respect them. Secondly, what works for one system might not work for another. Every network configuration is unique. Furthermore, I am not providing any specific technical instructions; this is a conceptual overview. Always exercise caution and prioritize security. That said, let's delve further.
Navigating the Digital Maze: The Conceptual Approach
Think of this as a series of intelligent compromises. You aim to create a seamless experience. First, consider the context: what specific restrictions are most hindering your work or personal productivity? Is it website access? Is it software limitations? Identify the pain points.
The Art of Strategic Compliance
Perhaps your need isn’t to bypass security but to optimize its usage. Explore the permitted avenues. Does your company offer any officially sanctioned methods for accessing necessary resources? Maybe there's a web portal for certain applications. Maybe a company-issued application that allows personal use on your work device. Always check the policies first.
Unlocking Network Freedom: Leveraging Existing Tools
Consider using other tools to bridge the gap. Think about your web browser’s capabilities. Many browsers have extensions and proxy settings. Perhaps you can use one. Similarly, cloud storage services can also facilitate file transfer. However, always maintain ethical and legal guidelines.
The Power of Information and Research
Staying informed is paramount. Research your work laptop’s setup. Search for your specific VPN version. Then, understand the existing network policies. Knowledge empowers. Online forums and communities can provide invaluable insights. Search specifically for your company's IT team. However, always verify any information gleaned from external sources. Not all advice is good advice.
Maintaining Digital Harmony: An Ethical Compass
Throughout this process, ethical considerations are essential. Always prioritize your company's security. Never attempt to compromise sensitive data. Your goal is seamless access, not malicious exploitation. Think before you act. Remember the underlying goal. Do not create a security breach.
The Long Game: Building Your Digital Resilience
This isn't a one-time trick. It's about developing a robust strategy. Regularly review your access points and adapt to changes. Stay informed. Keep your knowledge up-to-date. Think of it as a continuous learning experience. Your digital resilience will improve.
Important Disclaimer and Final Thoughts
I must reiterate that I am not providing specific instructions or encouraging any activity that violates your company's policies. This is a conceptual discussion. Always prioritize security and ethical conduct. Remember your obligations. Ultimately, reclaiming your laptop's potential requires a balance of knowledge, strategy, and respect for the rules. Now, go forth, explore, and find your own path to laptop freedom. Remember, every situation is different and needs to be assessed on its own terms. Hopefully, this gives you some guidance.
Unleash Your Potential: The BEST Laptop for Work & Play!Here's your article:
Unlock Your Work Laptop NOW! (GlobalProtect Bypass Secret)
Okay, let’s be honest, we've all been there. Stuck at home, desperately needing that crucial document, or yearning to stream something on a break, only to be thwarted by the iron grip (or perhaps the digital velvet glove) of GlobalProtect. That pesky VPN, the digital gatekeeper of your work laptop, can feel like a brick wall when all you want is a little freedom. But fear not, because we're diving deep into the wilderness of work-from-home restrictions, and we're going to uncover some strategies – some secret whispers, if you will – to help you reclaim your laptop. This isn't about breaking the law, mind you; it's about understanding how things work and finding ways to navigate the terrain, safely and ethically. Are you ready to become a digital explorer? Let’s go!
1. The GlobalProtect Glitch: Why Is My Laptop Locked Down?
First things first, let’s understand the enemy. GlobalProtect, created by Palo Alto Networks, is a VPN client designed to secure your connection to your company's network. Think of it as a digital body armor for your data. It encrypts your internet traffic, protects against threats, and makes sure your work laptop behaves according to company policy. This is all fantastic… if you're at work. But at home? It can feel like a straightjacket. The restrictions are many, and the reasons are simple: data security, compliance, and maintaining control over company assets.
2. Understanding the Rules of Engagement: Your Company's Policy Matters
Before we even think about a workaround, we have to acknowledge one crucial truth: your company's policy is king. Ignoring it is like ignoring the rules of a game; you'll likely get penalized. Always check your company's IT policies concerning the use of personal devices and VPN configurations. Some companies are more flexible than others, and some might even allow certain configurations for personal use during off-hours. Knowing the rules is the foundation of responsible digital exploration.
3. The Authorized Route: Always the First and Foremost Consideration
Before even considering any other options, have you consulted your IT department? This is the safest, most legitimate path. They might have solutions already in place, like allowing you to connect to specific websites while on the VPN, or even having a separate, less-restrictive network profile for personal use. Open communication with IT is paramount; they are, after all, the gatekeepers of your digital realm.
4. The Stealth Mode: Utilizing Your Home Network Strategically
This is where things get interesting. One of the core principles of bypassing GlobalProtect (and similar VPNs) is to understand how internet traffic flows. If you can access a website or service without going through the GlobalProtect tunnel, you've won a small victory. This is often done by exploiting the lack of network segmentation, but it is important to remember that IT departments are rapidly stepping up their game, as this "secret" may not last long!
5. The Split Tunneling Option: A Balancing Act
Split tunneling is a configuration that allows some of your internet traffic to go through the VPN while other traffic bypasses it. This can be a lifesaver, but it's also a double-edged sword. While it could give you access to your favorite streaming site, it also potentially exposes your work laptop to security risks. Always be extremely cautious, and be sure to follow your company's policies if they allow it.
6. DNS: Deciphering the Digital Map
DNS (Domain Name System) is like the internet's phonebook. It translates website names (like google.com) into IP addresses (numbers that computers use to communicate). Sometimes, the DNS settings configured by GlobalProtect can block the access to certain sites. A bit of a switch and it can let you gain access.
7. The Mobile Hotspot Gambit: A Temporary Escape
This is a classic, and it's often effective for a quick fix. Disconnect from your home Wi-Fi, and connect to your phone's mobile hotspot. This creates a separate network connection that isn't routed through the GlobalProtect VPN. This can let you stream videos or access certain sites, but be mindful of your data usage! Also, be aware of any company policies about using personal data on work equipment.
8. Proxy Servers: A Digital Middleman (Use With Caution!)
Proxy servers act as intermediaries between your computer and the internet. They can be configured to route your traffic through a different IP address, potentially bypassing some restrictions. However, using proxy servers can come with security risks, and you must always use a trusted provider or your data is at risk! Always be careful.
9. The "Safe Mode" Approach: Avoiding Trouble
Sometimes, just starting your computer in safe mode will allow you to bypass security software. However, this isn't a long-term solution, and you won't have all the functionality of your system. Moreover, it is rarely possible.
10. Remote Desktop Adventures: Accessing a Different Machine
If you have a home computer, you could use a remote desktop application (like Microsoft Remote Desktop or TeamViewer) to connect to it from your work laptop. This allows you to control your home computer and access the internet through it, effectively bypassing the GlobalProtect VPN and its restrictions.
11. The USB Tethering Method: Bridging the Networks
Similar to the mobile hotspot strategy, USB tethering allows you to use your phone's internet connection by connecting your phone to your laptop via a USB cable. This provides a separate network connection that bypasses GlobalProtect.
12. Understanding Network Segmentation: The Underlying Architecture
Understanding network segmentation is key. Your IT department may have set up distinct networks within the organization and by understanding those principles, you may be able to get what you want.
13. Troubleshooting Common Problems: When Things Go Wrong
Bypassing security measures can be frustrating. If you face technical issues, try restarting your computer, checking your internet connection, and reinstalling the GlobalProtect client. If all else fails, contact your IT department, who ideally should have all these issues fixed already.
14. Ethical Considerations and the Future of Security
Remember, while we're exploring these tactics, it’s vital to act responsibly. Don’t use these methods to do anything illegal or harmful. Always prioritize your company’s security policies. The more sophisticated security measures and VPN setups will continue to evolve, requiring you to stay informed about them!
15. The Takeaway: Reclaiming Your Digital Freedom (Responsibly!)
So, there you have it. A glimpse beyond the digital curtain of GlobalProtect. We’ve explored several avenues, from the straightforward (talking to IT) to the more creative (leveraging your home network, albeit cautiously). Remember, knowledge is power, but responsible application is crucial. The goal isn't to break the system but to understand it, and to find a balance between work and your personal digital freedom—all while keeping your company's data safe.
In conclusion, unlocking your work laptop from the clutches of GlobalProtect can seem like a challenge, but it's one that with knowledge and caution, you can navigate successfully. Remember, communication, understanding your company’s security protocols, and always prioritizing ethical behavior are key. Go forth, explore responsibly, and reclaim your digital freedom.
Principal Keywords: GlobalProtect Bypass, Work Laptop Access SEO Headline: Bypass GlobalProtect NOW: Unlock Your Work Laptop Secrets! Pathway: GlobalProtect Guide Meta Summary: Tired of GlobalProtect restrictions? Learn how to unlock your work laptop and regain your freedom using these secret GlobalProtect bypass strategies! Work Laptop Access. Image Alt Text: Unlock your work laptop from the restrictions of GlobalProtect. Image Caption: Reclaim your freedom: Unlocking your work laptop while respecting security protocols.
FAQs:
Is it Illegal to Bypass GlobalProtect?
Bypassing GlobalProtect itself isn't inherently illegal, but many factors influence the legality. It depends on your company's policies and the specific methods you use. Always adhere to your company’s guidelines.
Will I Get Caught if I Bypass GlobalProtect?
Yes, it's possible. Your IT department can monitor network activity and detect unusual behavior. The more sophisticated the workaround, the less likely you are to be caught, but no method is foolproof. Remember that your company may keep detailed logs/records.
Are There Security Risks Associated with Bypassing GlobalProtect?
Absolutely. Bypassing the security measures can expose your laptop and your company's data to threats. Always be cautious and take precautions.
What Should I Do if I Can't Access a Specific Website?
First, check if the website is blocked by your company's policy. Secondly, contact your IT department. They may have a way to access the site or have a workaround in place.
Is It Possible to Use Streaming Services While on GlobalProtect?
Possibly. If your company allows split tunneling and the streaming service isn't explicitly blocked, then streaming is possible but usually not the case.
GlobalProtect Connection Failed
By 5-Minute Videos GlobalProtect Connection Failed by 5-Minute Videos
After connecting to VPN I lose Internet Windows 11 Solution
By The Geek Page After connecting to VPN I lose Internet Windows 11 Solution by The Geek Page
Troubleshooting WiFi & GlobalProtect on MNPS Laptops
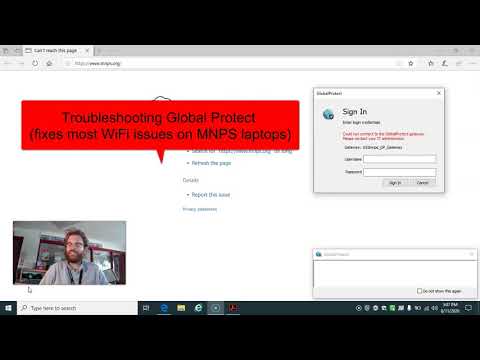
By Cumberland Elementary Troubleshooting WiFi & GlobalProtect on MNPS Laptops by Cumberland Elementary

Title: GlobalProtect Pre-logon using a machine certificate - PAN-OS 10.0.6
Channel: MB Tech Talker
GlobalProtect Pre-logon using a machine certificate - PAN-OS 10.0.6 by MB Tech Talker
Wifi Not Found
Here is the title: The Ultimate Guide to Mastering French Pastries: From Beginner to Baker Extraordinaire
The Alluring World of French Pastries: A Journey of Culinary Mastery
Welcome, fellow gourmand, to a delectable exploration of the sublime world of French pastries. Whether you are a novice eager to learn the fundamentals or a seasoned baker seeking to refine your skills, this comprehensive guide will serve as your invaluable companion. We will embark on a culinary adventure, delving into the heart of French patisserie, from the delicate flakiness of a croissant to the ethereal lightness of a macaron. Prepare to unlock the secrets behind creating these iconic treats, transforming your kitchen into a haven of exquisite aromas and unparalleled flavors.
Unveiling the Fundamentals: Essential Tools and Ingredients
Before we begin, let's equip ourselves with the necessary tools and ingredients. The success of any French pastry hinges on the quality of your components and the precision of your techniques.
Essential Tools:
- A High-Quality Kitchen Scale: Accuracy is paramount in baking. A digital scale ensures precise measurements, especially crucial for delicate pastries.
- Mixing Bowls (Various Sizes): Stainless steel bowls are ideal for whipping egg whites and creaming butter.
- Pastry Blender: Essential for cutting cold butter into flour, crucial for achieving the flaky layers in pastries like croissants and pâte feuilletée.
- Rolling Pin: A smooth, even rolling pin is essential for achieving uniform thickness in your dough. A French-style rolling pin, without handles, offers greater control.
- Bench Scraper: This versatile tool is invaluable for scraping dough from surfaces, dividing dough, and shaping pastries.
- Pastry Brushes: Use natural-bristle brushes for egg washes and glazes, ensuring even application.
- Piping Bags and Tips: Invest in a variety of piping tips for decorating cakes, filling pastries, and creating intricate designs.
- Oven Thermometer: Ovens can vary in temperature. Ensure your oven is calibrated correctly with a reliable thermometer.
- Baking Sheets: Use heavy-duty baking sheets for even heat distribution. Line with parchment paper for easy removal and cleanup.
Key Ingredients:
- High-Quality Flour: "T-45" or "T-55" flour is commonly used in France and has a lower protein content, making it ideal for tender pastries. All-purpose flour can be substituted, but the results may differ slightly.
- Unsalted Butter: Use high-quality, European-style butter with a high-fat content for optimal flavor and texture.
- Granulated Sugar: The foundation of sweetness in many pastries. Consider superfine sugar for certain applications, such as macarons.
- Eggs: Fresh, high-quality eggs are essential for binding ingredients, adding richness, and providing structure.
- Yeast (Fresh or Active Dry): Crucial for leavening pastries like croissants and brioche.
- Salt: Enhances the flavors of all ingredients.
- Water: Purified and chilled water is often used.
- Flavorings (Vanilla Extract, Almond Extract, etc.): These add complexity and character to finished pastries.
Embarking on the Classics: Mastering Iconic French Pastries
Now, let's explore the core recipes that form the bedrock of French pastry. Each recipe presents a unique opportunity to hone your skills and experience the magic of French baking.
The Croissant: Unveiling the Secrets of Flaky Perfection
Crafting a perfect croissant is a true art form, representing the ultimate test of patience and skill.
- The Détrempe (Dough): Combine flour, sugar, salt, and yeast in a bowl. Add cold water and mix until a shaggy dough forms. Knead the dough until smooth and elastic. Wrap in plastic wrap and refrigerate.
- The Beurre de Tourage (Butter Block): Flatten cold, high-quality butter into a rectangle. The butter must be cold but pliable.
- The First Turn (Simple Fold): Encase the butter block within the chilled dough. Roll out the dough into a large rectangle. Fold the dough in thirds, like a letter. This is the first "turn." Refrigerate for at least an hour.
- Second Turn (Simple Fold): Repeat the rolling and folding process. Refrigerate for at least an hour.
- Third Turn (Double Fold): Roll out the dough. Fold the dough in fourths, like closing a book. Refrigerate for at least an hour.
- Shaping: Roll out the dough. Cut into triangles. Gently stretch the triangles. Roll up each triangle from the base to the point.
- Proofing: Place the croissants on a baking sheet. Proof them in a warm, humid environment until doubled in size.
- Baking: Brush with egg wash. Bake at a high temperature, then reduce to a lower temperature to ensure even baking and crispness.
- Enjoy: The result will be a crispy, flaky, and buttery masterpiece.
Pâte à Choux: The Versatile Canvas for Creamy Creations
Pâte à choux is a deceptively simple dough capable of producing a variety of delightful treats.
- The Dough: Combine water, butter, salt, and sugar in a saucepan. Bring to a boil. Add flour all at once, stirring vigorously until a smooth dough forms. Cook over medium heat, stirring constantly, to dry the dough slightly.
- Eggs: Transfer the dough to a mixing bowl. Beat in eggs, one at a time, until the dough is smooth and glossy.
- Piping and Baking: Pipe the dough into the desired shapes (eclairs, cream puffs, etc.) onto a baking sheet. Bake until golden brown and puffed.
- Filling: Fill with pastry cream, whipped cream, or other desired fillings.
The Macaron: Ethereal Delights Made Real
The macaron, known for its exquisite meringue-based shells and creamy fillings, requires precision and technique.
- Meringue: Whisk egg whites with a pinch of salt until soft peaks form. Gradually add sugar and whisk until stiff, glossy peaks form.
- Almond Flour and Powdered Sugar: Sift together almond flour and powdered sugar to remove any lumps.
- Macaronage: Gently fold the dry ingredients into the meringue. The batter should flow like lava, not too thick or too thin.
- Piping and Resting: Pipe the batter onto a baking sheet. Let the macarons rest until a skin forms on the surface.
- Baking: Bake at a low temperature until the shells have "feet" and are cooked through.
- Filling: Fill with ganache, buttercream, or other desired fillings.
Exploring Beyond the Basics: Advanced Techniques and Flavor Combinations
Once you have mastered the core recipes, you can expand your repertoire and explore more advanced techniques.
Pâte Feuilletée (Puff Pastry):
The ultimate test of patience, a properly made pâte feuilletée is a symphony of flaky layers. The process involves multiple turns, refrigerating the dough between each turn, to develop the characteristic flakiness.
Flavor Infusion:
Experiment with different flavors by adding cocoa powder, spices, or extracts to your doughs and fillings.
Glazes and Decorations:
Elevate your pastries with elegant glazes, intricate piping, and edible decorations.
Troubleshooting Common Issues:
- Croissants: If your croissants fail to rise, check the freshness of your yeast and ensure proper proofing.
- Macarons: Feet that are too small or absent can indicate over-mixing the batter or an oven that is too hot.
- Pâte à Choux: If your cream puffs are flat, use the correct proportions of ingredients and bake them thoroughly.
Embracing the French Pastry Tradition: A Culinary Legacy
French pastry is not just about recipes; it's about a tradition of excellence, a dedication to quality ingredients, and a passion for creating beauty and flavor. It’s a journey of constant learning, experimentation, and refinement. Embrace the process, relish each success, and learn from every challenge. The world of French pastries awaits, filled with endless possibilities. Bon appétit!
